Explain the Different Types of Authentication Methods
HTTP Authentication Schemes Basic Bearer The HTTP Protocol also defines HTTP security auth schemes like. There are various ways a user can be authenticated - some of which include Session-based authentication Cookie-based authentication Token-based authentication Claims-based authentication and HyperText Transfer Protocol HTTP authentication mechanisms.
It refers to password-based authentication.

. Like 2FA MFA uses factors like biometrics device-based confirmation additional passwords and even location or behavior-based information eg keystroke pattern or typing speed to confirm user identity. If network authentication services are available to you then Oracle can accept authentication from the network service. Physiological technique makes use of face fingerprint voice retina Iris.
As far as authentication is concerned there are mainly three types of WLAN authentication methods that are used today. It requires the password for the particular username. Lets review the 4 most used authentication methods used today.
It is the simplest way of authentication. 4 Most Used Authentication Methods. Multi-Factor Authentication MFA As the name suggests Multi-Factor Authentication involves at least two different kinds of authentication factors to elevate security levels.
Authentication process can be described in two distinct phases - identification and actual authentication. Within these main types of authentication is a number of common solutions that you may wish to use. Passwords can be in the form of a string of letters numbers or special characters.
Some of the most common authentication methods that youre likely to encounter include. Unlike Two-Factor Authentication that is limited to two factors only MFA use cases can involve three or more of them. In process of authentication the key K must not be revealed to a third party user.
This solution is a property-based authentication like a card with an RFID chip in it. If the password matches with the username and both details match the systems database the user will be. Identification phase provides a user identity to the security system.
There are a number of authentication methods that can be used to confirm the identity of users who connect to. Three 3 Types of Authentication Example answer. Time-based One-time Password Algorithm based on the current time HMAC-based One-time Password Algorithm based on a counter.
Something the user knows something the user is and something the user has. These include both general authentication techniques passwords two-factor authentication 2FA tokens biometrics transaction authentication computer recognition CAPTCHAs and single sign-on SSO as well as specific authentication protocols including Kerberos and SSLTLS. The advantage to this type of authentication.
These methods are used in applications that leverage two-factor authentication. Two perform biometric authentication two techniques are used physiological techniques and behavioral techniques. Explain three different 3 types of authentication methods developed and distributed to users as per business requirements.
The list below reviews some common authentication methods used to secure modern systems. Systems users messages and applications. In behavioral technique persons behavior is observed to ensure that he or she is not trying to claim to be someone else.
Now that we know what authentication is lets see what are the most used authentication methods in REST APIs. A user enters the username and password then both the server and the client generates a one-time password. Authentication Types The most frequent types of.
Every time a user interacts with an authentication server in addition to any explicit credentials they present they or their devices implicitly present a number of different signals. Prominent examples include Kerberos Public Key Infrastructure PKI the Remote Authentication Dial-In User Service RADIUS and directory-based services as described in the following subsections. Common biometric authentication methods include fingerprint identification voice recognition retinal and iris scans and face scanning and recognition.
These authentication types apply to all classes of entity that require authentication. Contextual authentication collects signals like geolocation IP address and time of day in order to help establish assurance that the user is valid. Write your response in 200-250 words.
The various methods are. Answer may vary. Authentication can be accomplished by proving knowledge of this shared symmetric key.
Multi-factor authentication is a high-assurance method as it uses more system-irrelevant factors to legitimize users. Authentication using public keys-. Basic authentication is a commonly used term that most people probably understand already.
Passwords are the most common methods of authentication. Student must include the following information. Three categories in which someone may be authenticated are.
Authentication using symmetric keys-Suppose two users share a symmetric key K and this key is only known to both.
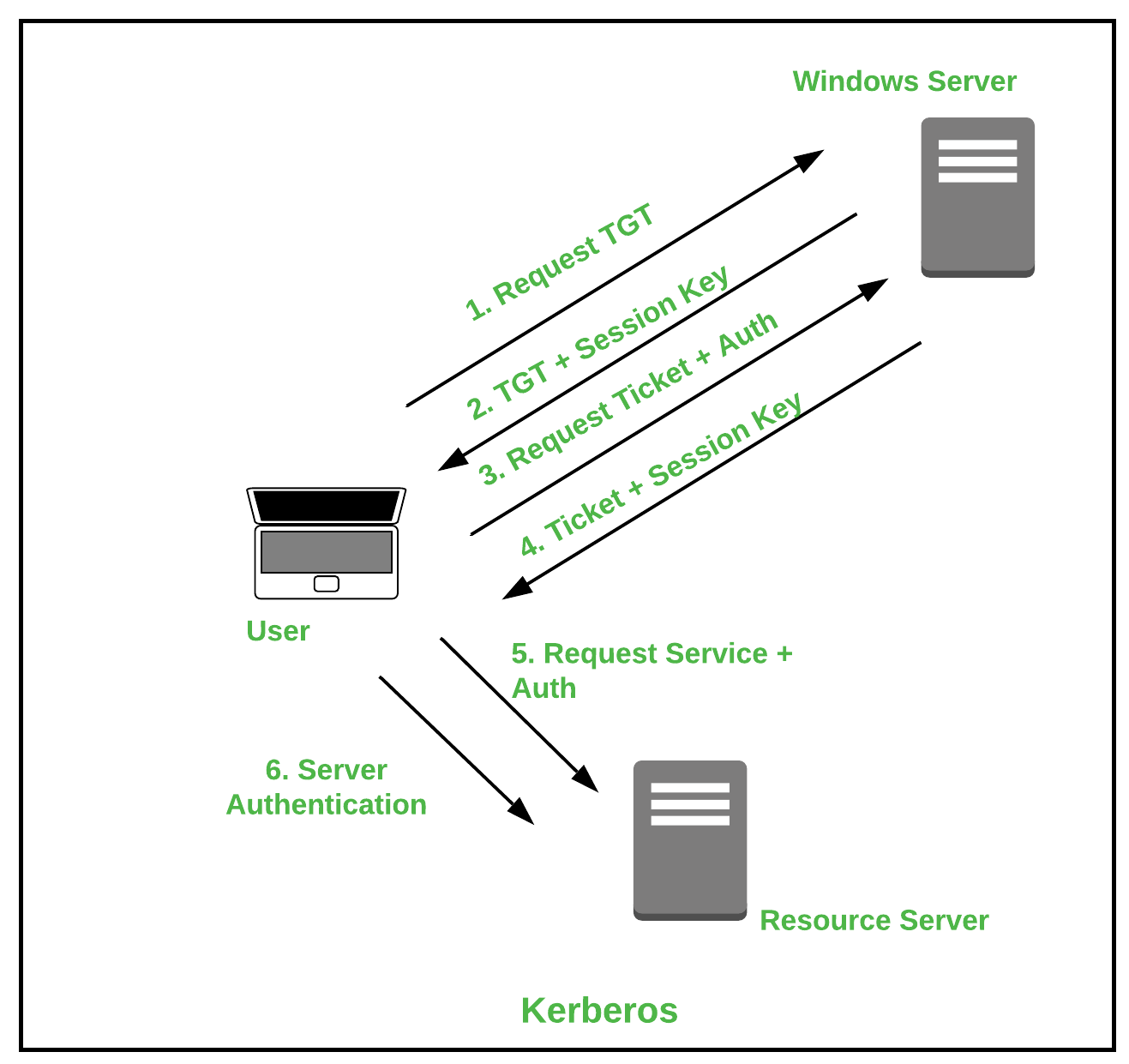
Types Of Authentication Protocols Geeksforgeeks


No comments for "Explain the Different Types of Authentication Methods"
Post a Comment